
The first step and in every situation is brute-force directory =). And my result when i did it

And i found a special directory so let’s access to it and you will see a php folder. In php folder, we can see a file php backup.

Click into this file and we have a source code backend php.

I sure that we can exploit website with PHP Object Injection via Unserilize when I check cookie named tracked. And my cookie when decode with urldecode

So i write some code php to get serialize object, encode it with urlencode and assign it to cookie. But before do it, i will talk about the code above.
We have a variable $counter_output_path contains directory to excute some functions and i feel __destruct function seem to be exploit. __destruct function will excute when the object is destructed or the script is stopped or exited. So i will use find command into this funtions to crawl dirctory contains flag file via unserialize function.
My code to get serialize and after try to guest directory =(:

And it give me a payload

I use it to assign to the cookie and i have flag directory

OK! Now my next step is find the ways to cat this file =). Review to php code above. We can use some trick to use find command read flag file.
Finally, i spent about 30 minutes to research and find the ways to bypass escapeshellcmd.
I found a payload to excute code in server.

But if you use original code, you will fail =). Because escapeshellcmd function will add a couple slash before your slash. But if you only input ;, it will replace become \;.
So Cool!! Use this code to get object and get flag!

And i retrive payload
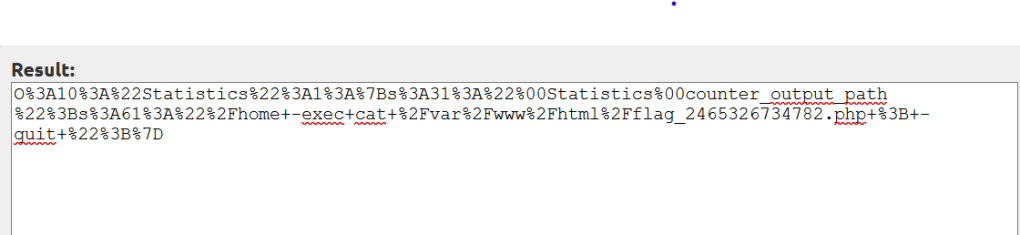
And change it with cookie and get flag




![[CVE-2022-3133] Draw.io – XSS leads to RCE](https://nhienit.files.wordpress.com/2023/06/android-chrome-512x512-1.png?w=512)
Bình luận về bài viết này